This seems to be a chicken-egg problem.
The most common task using sudo is installing and removing software.
sudo apt-get purge <appname>
But sudo itself can be removed.
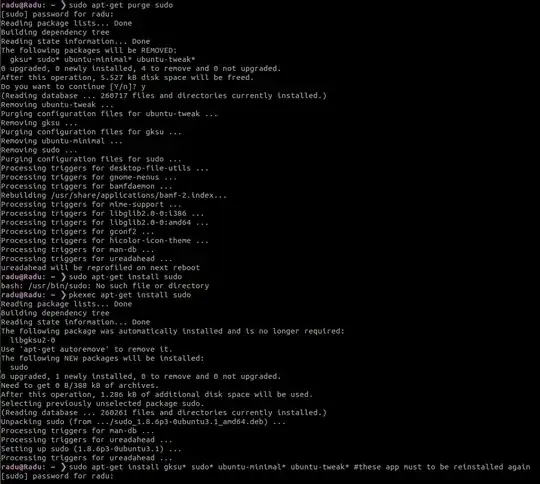
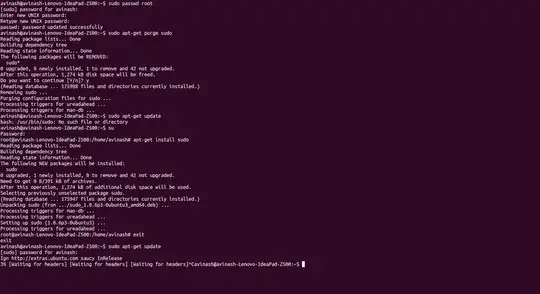
sudo apt-get purge sudo # Do not run this command on production computers!
This is where the fun comes
ubuntu@ubuntu:~$ sudo
bash: /usr/bin/sudo: No such file or directory
Although it's obvious that no person in his right mind will purge sudo (other than me), someone can be fooled to run this command (not directly, in its hex mode, or whatever it's called) or a person could SSH in disguised as tech guru and do the mess.
So is there a way of reinstalling sudo?